How To Know if Your WordPress Hosting Has Good Security

If you’ve ever shopped for web hosting, you know every provider swears their security is “rock solid.” Which sounds reassuring… until you realize “rock” can mean granite or it can mean decorative garden pebble.
The truth is, “secure hosting” can mean anything from “we installed an SSL certificate once” to “we have a 24/7 security operations center scanning for threats you’ve never even heard of.” And unless you know what to look for, you might be paying for granite while actually getting gravel.
When WordPress sites get compromised or hacked, it’s not usually because their owners are reckless. It’s because their hosting security is basic or lax when the business should have upgraded to something more strategic. So, instead of just wondering if your hosting is secure (a question almost every provider will say yes to), the better question is this:
What level of security am I getting — and does it match the value of my website and my business needs?
In this guide, we’ll walk you through the WordPress Hosting Security Maturity Model, a five-stage framework that takes you from basic survival measures to bulletproof, business-aligned protection.
Figure out where you stand today, what gaps you may be living with, and whether your hosting is protecting your growth.

The Security Maturity Reality Check
When a hosting company says they’re secure, they probably aren’t lying. They just might not be telling you the whole story. It’s like when a restaurant menu says “locally-sourced.” Sure, the eggs came from a farm 10 miles up the road. But the rest of your dinner? Unloaded from a freezer truck.
That’s the problem with generic security claims: without context, they’re meaningless. SSL certificates, firewalls, backups —these are the baseline. They keep your site from collapsing under the most obvious threats, but they don’t guarantee it’s safe against the kind of attacks that can bring your business to its knees.
Why WordPress Hosting Security Is Different
Not all hosting environments secure WordPress the same way. Generic hosting protects at the server level, but WordPress-specific hosting bakes in protections tuned for the exact ways WordPress sites get attacked —plugins, themes, logins, and configuration files.
Here’s how the two approaches compare:
The Hidden Costs of Being “Secure Enough”
Operating below your security needs can cost you in the real world.
- Downtime that kills sales: In a recent survey of 500 business professionals, companies reported losing an average of five hours per month to downtime. One in five said they lose over $2,500 per month because of it.
- Breaches that drag you down: Nearly half of businesses surveyed experienced hacking attempts because of poor hosting security, and 32% suffered actual data breaches.

Security Is a Growth Enabler
Too many folks treat security as a nuisance or a box to check. That’s short-sighted.
Instead, think of it as insurance for growth:
- Fast, reliable sites boost SEO rankings and keep customers happy.
- Solid compliance and data protection open doors to new markets and contracts.
- When you’re confident that hosting has your back, you can focus on scaling, not patching security holes.
These aren’t just technical wins; they’re business moves.
The 5-Stage Security Maturity Model: From Basic to Bulletproof
Website security isn’t a binary switch you flip on or off. It’s more like a dimmer. At the lowest setting, you can still see what’s in front of you —but you have room to turn up the lights to see much more clearly.
The WordPress Hosting Security Maturity Model is our way of turning the lights all the way up. It helps you figure out exactly where your hosting stands today, what threats you’re protected against, and where the gaps are hiding.
Each level builds on the one before it, starting with bare-minimum survival features and climbing all the way to military-grade defenses most small businesses will never actually need (and shouldn’t pay for).
The goal is to match your hosting security to your actual business risk, so you’re investing in the protections that make sense for your traffic, data, and growth goals.
Let’s start at the bottom rung and work our way up.
Level 1: Basic Protection

This is the “camping in your backyard with a flashlight” stage of hosting security. You’ve got some gear —enough to get through a quiet night —but if a storm hits or the raccoons get curious, you’re not exactly equipped to fend them off. At this stage, plugin and theme updates are entirely manual. Many WordPress sites fall behind here, leaving them open to exploits that have already been patched upstream.
At this level, your host is giving you the absolute bare necessities:
- SSL/TLS encryption: That little padlock in the browser that says your site’s connection is secure. This is table stakes; Google’s been favoring HTTPS sites for years.
- Basic backups: Once a day or so, and usually stored right on the same server (which is like keeping your spare house key under the welcome mat).
- Shared hosting environment: Your site likely lives on the same server as dozens or hundreds of others, sharing resources (and in some cases, vulnerabilities).
What It Protects You From
Level 1 can shield you from casual drive-by threats, like data snooping over public Wi-Fi, visitors getting “Site Not Secure” warnings in their browser, and minor mishaps like accidentally deleting a page or two.
What It Doesn’t Protect You From
Anything targeted, persistent, or automated. A brute-force login attack? A vulnerable plugin exploit? A spike in traffic that crashes your server? At Level 1, you’re basically hoping those things don’t happen to you.
Who It’s For
If you’re running a personal blog, a static brochure site for a local club, or you’re just dipping your toes into WordPress with minimal traffic and zero e-commerce, Level 1 might be fine…for now.
The Hidden Cost of Staying Here
Waiting until something happens to upgrade your security is a gamble. Once you start collecting customer data, selling products, or getting regular traffic, you’ve outgrown Level 1. And if you don’t move up the ladder, you could find yourself cleaning up a mess that costs more than a year of better hosting.
Questions To Ask Your Host:
- How often are backups taken, and where are they stored?
- Is SSL included and automatically renewed?
- How quickly can I restore my site from a backup if something goes wrong?
If their answers are fuzzy (or involve extra fees for basics), you’re looking at the minimum possible investment in security. That’s fine for a hobby site, but not for a business you actually want to grow.
Level 2: Proactive Defense

If Level 1 is camping in your backyard with a flashlight, Level 2 is at least checking the weather forecast before you pitch the tent. You’re putting up some defenses to keep trouble from reaching you in the first place.
At this stage, your host should be providing tools that actively monitor and block common threats, not just clean up after them.
- Web Application Firewall (WAF): Filters malicious traffic before it reaches your site. A good WAF blocks common attacks, like SQL injection and cross-site scripting. A WAF tuned for WordPress blocks common vectors like XML-RPC abuse, brute-force attempts on wp-login.php, and known plugin exploit signatures — things generic firewalls might miss.
- Automated malware scanning: Regular sweeps that look for malicious code hiding in your files.
- Brute-force protection: Login attempt limits or two-factor authentication to keep automated bots from hammering your login page.
- Basic performance monitoring: Alerts for downtime or unusual traffic spikes so you can react quickly
What It Protects You From
Level 2 helps fend off opportunistic hackers, automated botnets, and the more obvious plugin vulnerabilities that attackers scan the internet for. It also buys you time. If something suspicious pops up, you’ll hear about it before it spirals into a major incident.
What It Doesn’t Protect You From
Advanced, targeted attacks. At Level 2, your defenses are still largely “off the shelf,” which means determined attackers can find ways around them. There’s also limited isolation between your site and others on the same server, so a breach elsewhere could, in rare cases, spill over.
Who It’s For
Small to medium-sized businesses with active content updates, modest e-commerce activity, or growing mailing lists. If you’re collecting any customer data (even just emails), you should be at least here.
The Hidden Cost of Staying Here
You’re protected against the low-hanging fruit attackers go after first, but the more valuable your site becomes, the bigger the target on your back. Staying at Level 2 too long is like locking your front door but leaving the windows open.
Questions To Ask Your Host:
- How is your WAF configured, and is it updated automatically?
- How often do you scan for malware, and what happens if you find some?
- Do you limit login attempts or offer 2FA?
Level 3: Advanced Protection

If Level 2 is locking your doors and setting an alarm, Level 3 is hiring a security guard who actually knows how to spot trouble before it starts. At this stage, your hosting is actively isolating, monitoring, and adapting to stop new ones in their tracks.
- Advanced threat detection: Constant scanning that doesn’t just look for known malware signatures, but also suspicious behavior patterns.
- Account and process isolation: Each site or account on the server is walled off so a breach in one can’t spill into another.
- DDoS protection: Defenses against massive floods of traffic meant to overwhelm your site.
- Staging environments: Let you safely test updates and changes before pushing them live, reducing the risk of breaking your site or introducing vulnerabilities. Staging environments are especially critical for WordPress. With so many plugins and themes interacting, updates can break your site if you don’t test them in a sandbox first.
- More frequent backups, stored off-server: If something does go wrong, you can restore from a clean backup that isn’t sitting right next to the problem.
What It Protects You From
Level 3 stops most opportunistic and many targeted attacks. Botnets, large-scale automated intrusion attempts, and cross-site contamination are much less likely to get through. You also gain resilience against performance-related attacks, like DDoS floods that can take down unprotected sites.
What It Doesn’t Protect You From
Highly specialized attacks aimed directly at your business, or threats that require enterprise-level compliance and monitoring. This is a strong middle ground, but it’s not designed for organizations dealing with regulated data or state-level threat actors.
Who It’s For
Revenue-critical websites, like thriving e-commerce stores, membership platforms, agencies hosting multiple client sites, or any business where downtime means losing real money and trust.
The Hidden Cost of Staying Here
Level 3 can feel “good enough” for a long time, and for many businesses, it is. But if you expand into regulated markets, start handling more sensitive customer data, or experience rapid growth, the gaps between Level 3 and enterprise-grade protection start to matter.
Questions To Ask Your Host:
- Do you isolate accounts at the server level?
- How quickly can you mitigate a DDoS attack?
- Are backups stored offsite and encrypted?
- Can I create a staging environment for testing?
Level 4: Enterprise-Grade
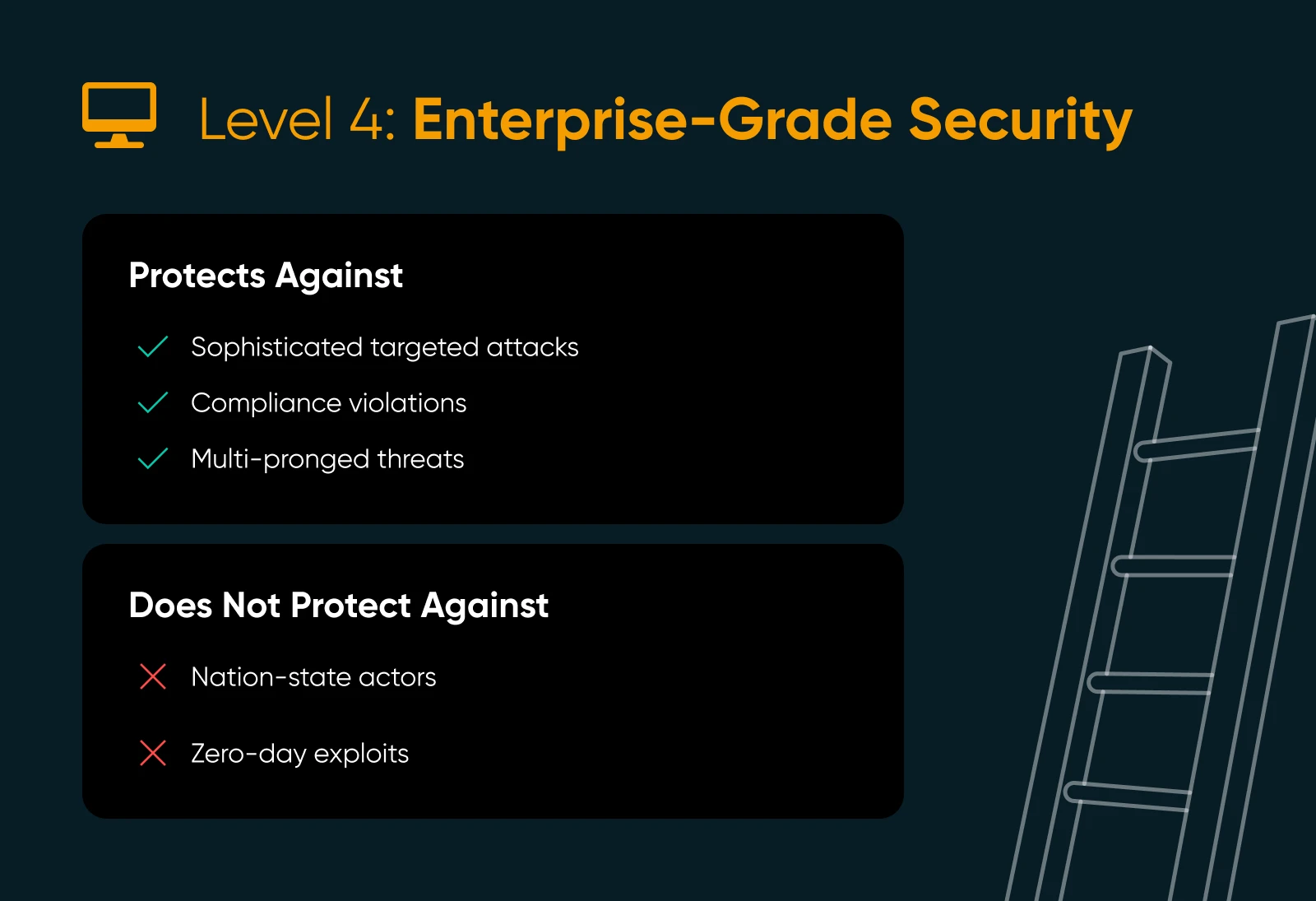
At this point, you’ve moved from having a capable security guard to running your own 24/7 command center. Level 4 is about strategy —not just stopping attacks, but anticipating them, meeting strict compliance requirements, and proving you’ve done it.
- Security Operations Center (SOC) monitoring: Around-the-clock human oversight, backed by advanced tooling to spot and respond to incidents in real time.
- Compliance-ready infrastructure: Support for industry standards like PCI DSS (for credit card data) or GDPR (for personal data protection), with clear documentation. Compliance matters most for WordPress ecommerce or membership sites. If you’re running WooCommerce and processing credit cards or storing personal data, enterprise-level security can help you meet PCI DSS and GDPR requirements.
- Advanced logging and audit trails: Comprehensive records of user activity and server events for security reviews and forensic investigations.
- Customizable security rules: The ability to tailor firewall and monitoring configurations to your specific risk profile.
What It Protects You From
Sophisticated targeted attacks, compliance violations, and the kind of multi-pronged threats that can cripple a business without proper oversight. Level 4 gives you the receipts to prove you’re secure to regulators, partners, and customers.
What It Doesn’t Protect You From
Nation-state actors or the most cutting-edge zero-day exploits. Level 4 is extremely robust, but there’s still a final tier for organizations with the highest stakes.
Who It’s For
Established e-commerce brands, SaaS companies, financial service providers, healthcare organizations, or anyone who must meet compliance requirements while maintaining uninterrupted service.
The Hidden Cost of Staying Here
If you truly operate in a high-risk, high-value environment (think confidential R&D data or government contracts), even Level 4’s comprehensive defenses might leave a small but critical gap.
Questions To Ask Your Host:
- Do you provide compliance documentation and assistance?
- What’s your process for real-time incident response?
- How long are logs retained, and are they tamper-proof?
Level 5: Military-Grade, Bulletproof Security

This is the digital equivalent of a fortified bunker with biometric locks, armed guards, and an air filtration system that could survive the apocalypse. While most small businesses will never need Level 5, large WordPress multisite networks or government/finance organizations running WP applications sometimes require zero-trust and AI-driven defenses. This level offers:
- Zero-trust architecture: Every user, device, and connection must verify itself at every step, no exceptions.
- AI-driven threat detection: Machine learning models flag anomalies in real time, catching even brand-new attack methods.
- Custom, client-specific security infrastructure: Dedicated servers, fully isolated environments, and bespoke firewall rules.
- Continuous penetration testing: Regular, simulated attacks to find weaknesses before real attackers do.
What It Protects You From
Almost everything short of someone physically walking into your data center with bad intentions. This level is designed to withstand advanced persistent threats, sophisticated zero-day exploits, and the most resourceful adversaries.
What It Doesn’t Protect You From
Human error. Even the most advanced systems can’t save you if someone uploads malware disguised as a spreadsheet or gives away credentials in a phishing scam.
Who It’s For
Government agencies, defense contractors, multinational corporations in regulated industries, or companies handling extremely sensitive intellectual property.
The Hidden Cost of Staying Here
Ironically, over-securing your hosting can be as inefficient as under-securing it. Level 5 protection is expensive and complex, so if you don’t need it, you’re burning capital you could invest elsewhere in your business.
Questions To Ask Your Host:
- Do you support zero-trust network segmentation?
- Can AI models be tailored to my specific environment?
- How often are penetration tests performed, and who conducts them?
Your Security Maturity Action Plan
Now that you know the five levels, it’s time to figure out where you are — and whether that’s good enough for your business today (and tomorrow).
Follow this four-step action plan to find out.
Step 1: Self Assessment
Ask yourself:
- What security features does my host provide at the server level?
- How quickly would I know if one of my plugins introduced a vulnerability?
- How fast could I recover from a complete site wipe?
- Can I restore my entire WordPress site — core, plugins, themes, database, media — in one click?
If you’re unsure about any of these answers, your security maturity level is probably lower than you think.
Step 2: Gap Analysis
Match your current level to the threats it doesn’t cover. For example:
- At Level 1, you’re exposed to brute-force attacks and malware.
- At Level 2, you still lack isolation and advanced threat detection.
- At Level 3, you’re missing compliance tools and custom security rules.
Knowing your gaps lets you decide whether you’re accepting those risks or ready to close them.
Step 3: Upgrade Roadmap
Transitioning from Level 1 to Level 4 overnight can be expensive and overwhelming. Instead, focus on the next logical step.
If you’re on basic shared hosting, start by adding a WAF and automated malware scans to get to Level 2. If you’re already there, push for account isolation and DDoS protection to get to Level 3.
Step 4: ROI Check
Does the investment make sense for your business? If better security prevents even one major outage or breach, the cost often pays for itself many times over. For example, spending $50 a month on upgraded hosting to avoid a $2,500 downtime loss isn’t an expense — it’s insurance that earns its keep.
From Survival Mode to Strategic Security
Your hosting security maturity level is a business decision. Running a high-traffic store on Level 1 is like parking your Ferrari in a sketchy alley. On the other hand, paying for Level 5 when you run a small local blog is like hiring the Secret Service to watch your garden shed.
The sweet spot is finding the level that protects your revenue, reputation, and growth without overspending on features you’ll never use.
At DreamHost, we build security into every layer of our WordPress hosting, from free SSL and automated updates to daily backups, malware scanning, and WordPress-trained support. Explore DreamHost WordPress hosting, find your perfect fit, and give your site the protection it needs to grow with confidence.

DreamShield
Protect Your Website with DreamShield
Our premium security add-on scans your site weekly to ensure it is free of malicious code.
Enable DreamShield



