Scary Hosting Tales: 10 Security Risks Haunting 2025

TL;DR: In 2025, the scariest website security risks haven’t come from WordPress core — they’ve come from vulnerable plugins, neglected themes, and unpatched server software like OpenSSH and PHP on Ubuntu.
These are the 10 most impactful vulnerabilities so far this year, including how they worked and what lessons site owners and developers should take away. The bottom line: consistent updates, careful role management, and attention to security advisories are what keep your hosting stories from turning into horror stories.
It always starts the same way.
A late-night ping. A panicked client. A WordPress site that was working fine yesterday, but is now coughing up error logs and redirecting visitors to a sketchy pharmacy domain. In your mind, all you can hear is the screeching violins from a horror soundtrack.
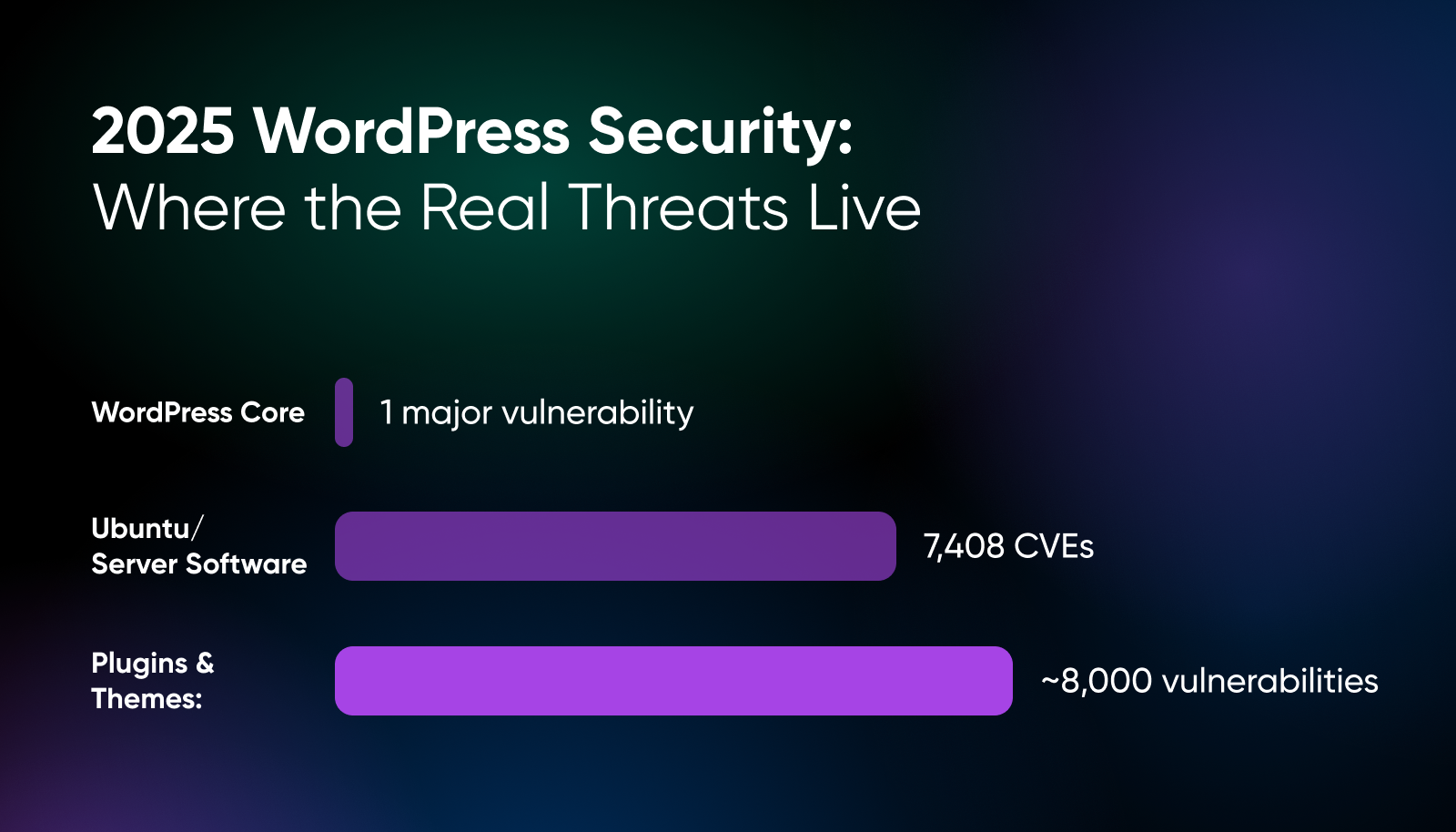
Most scary hosting tales aren’t caused by the ghosts and monsters of spooky season fame. They come from vulnerabilities left unpatched just a little too long. In 2025, the real danger hasn’t been WordPress core (which has only had one notable issue this year to date), but rather the plugins, themes, and server software that power your site.
That’s why we’re here, flashlight in hand, to walk you through the top 10 vulnerabilities that sent shivers down developers’ spines this year. These aren’t cautionary tales meant to scare you away from the web. They’re field notes from the front lines —lessons you can use to keep your hosting stories from turning into horror stories. Let’s dive in.
What Does the 2025 Threat Landscape Look Like for WordPress Plugins and Ubuntu Packages?
Plugins and themes are where almost all the WordPress risk lives. In 2025, WordPress core has seen only one major vulnerability so far, but the plugin and theme ecosystem has already produced close to 8,000 vulnerabilities as of September (when we wrote this article).
Mid-year reports confirm not only the high volume, but high real-world exploitability. 6,700 vulnerabilities were identified in the first half of the year, with 41% classified as exploitable in real-life attacks.
Ubuntu’s security notices (USNs) provide regular, transparent updates for issues across supported releases. Many of those USNs cover critical software commonly used in hosting environments (PHP, OpenSSH, libraries like libxml2, etc.). Between January and August 2025, Canonical published 829 USNs covering 7,408 unique CVEs across the supported releases. That already outpaces all of 2024, which saw 884 USNs addressing 5,611 CVEs.
The pattern is clear: the volume of OS-level vulnerabilities is accelerating, often overlapping in risk with plugin and theme leaks.
So what can business owners take away from the threat landscape in 2025? There’s three primary things:
The 10 Scary Tales of 2025: What Went Wrong (and What Can We Learn From It)?
Below are the real vulnerabilities that shook the WordPress plugin ecosystem this year (so far). Keep in mind that these aren’t ancient history —many sites are still exposed unless patched.
1. Post SMTP
What happened: Version ≤ 3.2.0 of the Post SMTP WordPress plugin had a broken access control in one of its REST API endpoints (the get_logs_permission function). The function only checked if a user was logged in, not whether they had sufficient privileges (for example, Administrator).
Because of this, even Subscriber-level users could fetch email logs, view email bodies, and intercept password reset emails intended for higher-privilege users. Yikes!
Email logs often include sensitive details. Intercepting password resets means a low-privilege user could reset an admin’s password and take over the site. That turns what seems like a harmless plugin bug into full-site compromise.
Plus, Post SMTP is widely used, with over 400,000 active installations. A large slice of those sites were running vulnerable versions at the time of disclosure.
Key takeaway: Even simple checks (is_user_logged_in) aren’t enough for sensitive data. Privilege checks must match the sensitivity of the endpoint.
2. Essential Addons for Elementor
What happened: Versions ≤ 6.0.14 of Essential Addons for Elementor had a reflected Cross-Site Scripting (XSS) vulnerability in the popup-selector query argument. Input was not properly sanitized/validated before being embedded into page output. The flaw was fixed in version 6.0.15.
This plugin has over 2 million installations, so a vulnerability like this has a large potential reach. Reflected XSS can enable phishing, credential theft, token hijacking, or defacement if an attacker tricks a user into clicking a crafted URL. The scale of active installs means many sites were exposed.
Key takeaway: Popular plugin + simple input vector = widespread risk. A large install base magnifies even “just XSS” vulnerabilities.
3. WPForms Lite
What happened: WPForms Lite versions up to 1.9.5 were vulnerable to stored Cross-Site Scripting via the start_timestamp parameter. Authenticated users with Contributor role or above could inject scripts that persist and run whenever a user views a compromised page.
Because contributor-level access is often granted (or accidentally kept) on sites with multiple authors or team members, the risk was real. The ability to persist script injection means compromise can live until the site code or database is cleaned —not just a one-time reflected attack.
While the CVSS severity is “medium” (5.4) for this issue, persistent XSS is harder to detect, harder to scrub, and carries bigger consequences (cookie theft, privilege escalation, user trust loss) than many people realize.
Key takeaway: Stored XSS via lower role users is dangerous. Permissions matter, as does ensuring even “trusted” users aren’t automatically safe.
4. GiveWP
What happened: Versions of GiveWP before 3.19.4 contained a PHP Object Injection vulnerability. Input passed to certain unserialize functions wasn’t validated, allowing crafted payloads to be injected. Under some PHP configurations, this could enable attackers to trigger “magic methods” in classes, leading to Remote Code Execution (RCE).
GiveWP is one of the most popular donation plugins, powering over 100,000 active installations. Sites that rely on it for nonprofit fundraising could have had their servers hijacked, not just their front-end displays. That’s both a business continuity and trust disaster.
Key takeaway: Complex plugins like donation platforms handle sensitive data, which makes them prime targets. Always patch them quickly.
5. AI Engine Plugin
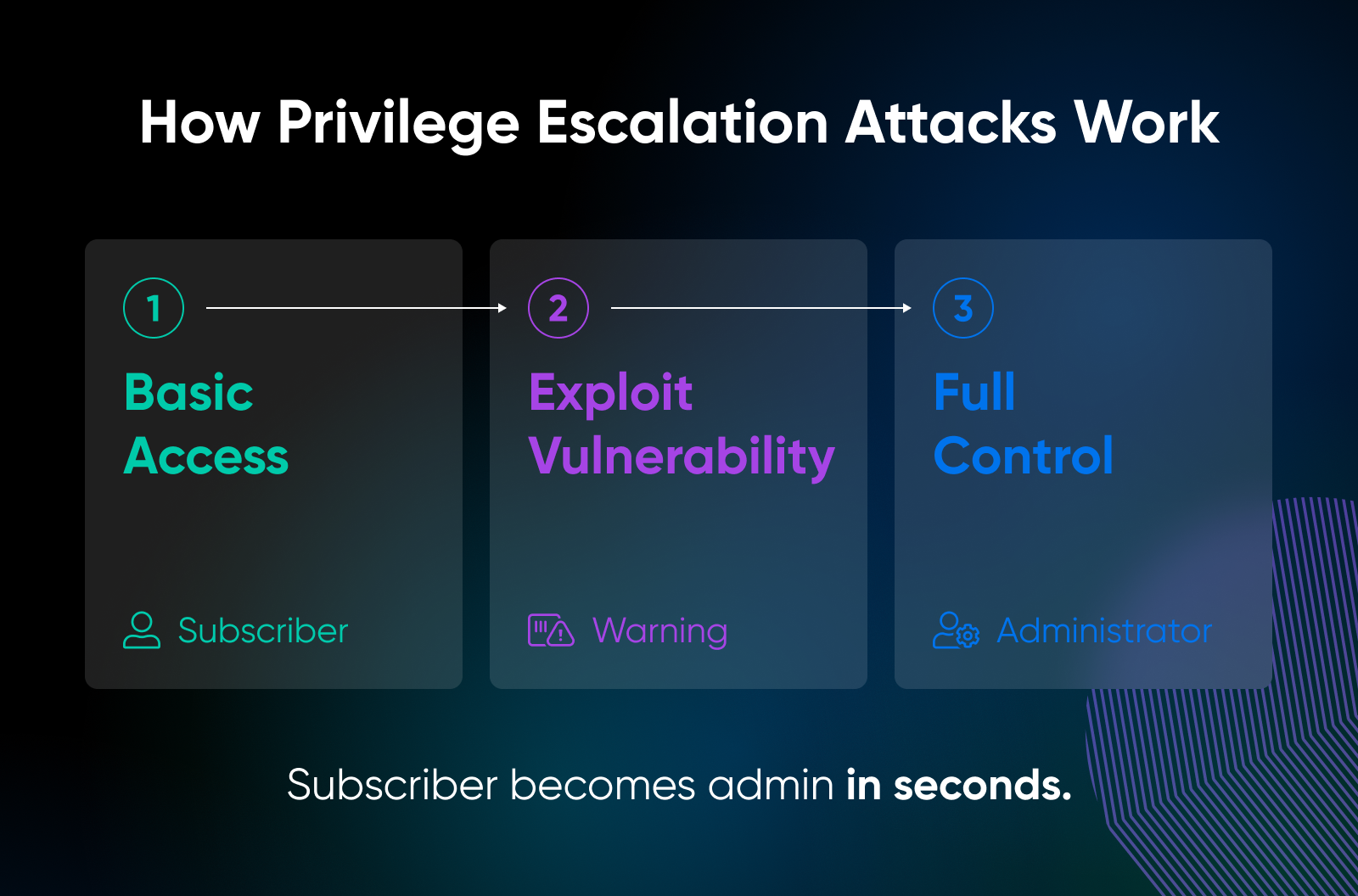
What happened: The AI Engine plugin by Meow Apps shipped a version that lacked access checks, allowing users with minimal roles to escalate their privileges. This meant an attacker who could register as a basic user could promote themselves to Administrator.
Privilege escalation vulnerabilities are among the most devastating because they subvert the trust model. A registered user (or in some cases even a bot creating a new account) could instantly gain control of the entire site. With AI Engine widely adopted to integrate OpenAI and other AI services, the blast radius extended to both marketing and production websites.
Key takeaway: Privilege escalation is scarier than XSS because it hands attackers the keys to your site. Role audits should be part of every monthly maintenance routine.
6. B Blocks Plugin
What happened: B Blocks, a WordPress plugin with tens of thousands of installs, had a critical flaw: missing authorization checks allowed unauthenticated visitors to create new administrator accounts. Unlike other privilege escalation bugs, this one didn’t require any user role or login at all.
Any attacker who knew the endpoint could spin up a brand new admin account. From there, they could install backdoors, export the database, or inject SEO spam links across the site. Because it didn’t require existing access, this bug was heavily exploited in the wild shortly after disclosure.
Key takeaway: Unauthenticated privilege escalation is as bad as it gets. Every site owner should regularly check their user list, even when they think everything is patched.
7. Motors Theme
What happened: The Motors theme, widely used for car dealership and auto marketplace sites, contained a privilege escalation flaw. The vulnerability allowed unauthenticated attackers to exploit weak checks in the theme code to gain administrator-level privileges.
Unlike small niche themes, Motors is commercial and heavily adopted. A compromised theme at this scale means thousands of business sites advertising inventory, payments, and customer leads are suddenly exposed. Privilege escalation here means attackers didn’t need to be clever — they could simply “walk in” and promote themselves.
Key takeaway: Themes can be as dangerous as plugins. If you bought a theme years ago and haven’t updated it, that theme may be your weakest link.
8. Database for Contact Form 7 / WPForms / Elementor Forms
What happened: The Database for CF7, WPForms, and Elementor Forms plugin had a critical Remote Code Execution / Denial of Service vulnerability. Versions ≤ 1.4.3 failed to sanitize user-supplied inputs, letting attackers inject malicious payloads through form submissions.
Because this plugin is an add-on to three of the most popular form builders, the exposure was amplified. An attacker could submit a “harmless” form but actually plant code on your server — a nightmare scenario for agencies managing multiple client sites.
Key takeaway: Even small “helper” plugins can bring down an entire stack. If you extend critical plugins with add-ons, patch them just as urgently as the main tool.

9. OpenSSH on Ubuntu 24.04
What happened: Canonical disclosed multiple OpenSSH vulnerabilities in 2025, including a forwarding bypass flaw where the DisableForwarding directive didn’t work as intended (USN-7457-1). Another advisory (USN-7270-1) addressed potential denial-of-service risks in client connections.
OpenSSH is one of the most foundational packages on Ubuntu servers. If SSH access is exposed, attackers can chain these bugs to gain persistence or disrupt availability. Many sysadmins assume SSH is safe by default, but vulnerabilities like these show that even the hardened core needs vigilance.
Key takeaway: Don’t assume critical packages are invulnerable. Even mature software like OpenSSH needs constant patching and config review.
10. PHP on Ubuntu
What happened: A vulnerability in PHP’s SOAP/XML parsing allowed crafted payloads with malformed namespace prefixes to trigger crashes. Canonical rolled this into USN-7648-1, which patched the issue on supported Ubuntu versions.
Many WordPress plugins and themes depend on PHP SOAP/XML functions for integrations (payment gateways, CRMs, marketing automation). A crash at the PHP interpreter layer means complete denial of service, and every site on that server could be affected.
Key takeaway: Server software flaws are just as threatening as WordPress bugs. If your PHP process dies, your site dies with it.
What These Tales Teach Us
Taken together, these 10 cases tell a consistent story: The scariest vulnerabilities in 2025 haven’t been exotic zero-days in WordPress core. They’ve been the everyday cracks in the walls: outdated plugins, neglected themes, and unpatched server software.
Three lessons stand out:

The takeaway isn’t to fear your software stack, but to respect it and take care of it. Every plugin, theme, or server package you install widens the surface area for attack. The difference between a scary hosting tale and a routine patch cycle is how quickly you spot and address those risks.
Security doesn’t have to be terrifying. With consistent updates, careful role management, and attention to advisories, you can keep the monsters at bay.

WordPress Hosting
Unbeatable WordPress Hosting
Reliable, lightning-fast hosting solutions specifically optimized for WordPress.
See More


